RC4
In cryptography, RC4 (also known as ARC4 or ARCFOUR meaning Alleged RC4, see below) is one of the most common software stream ciphers. It is used in popular protocols like Secure Sockets Layer (SSL) (to protect Internet traffic) and WEP (to secure wireless networks).
RC4 is known for being simple and quick, but attacks are likely to happen when the start of the output keystream is not removed, or one keystream is used twice; some ways of using RC4 can turn into very insecure cryptosystems such as WEP.
RC4 was created by Ron Rivest of RSA Security in 1987. While its official name is "Rivest Cipher 4", the RC abbreviation is also known to stand for "Ron's Code"[1] (see also RC2, RC5 and RC6).
RC4 was first created as a trade secret, but in September 1994 a description of it was posted to the Cypherpunks mailing list.[2] It was soon posted on the sci.crypt newsgroup, and from there to many websites on the Internet. The code was confirmed to be genuine(not fake) as its output matched that of proprietary software using licensed RC4. Because the algorithm is known, it is no longer a trade secret. The name "RC4" is trademarked, however. RC4 is often referred to as "ARCFOUR" or "ARC4" (meaning Alleged RC4, because RSA has never officially released the algorithm), to avoid possible trademark problems. It has become part of some commonly used encryption protocols and standards, including WEP and WPA for wireless cards and TLS.
The two main reasons which helped its use over such a big range of applications are its speed and simplicity. Uses of RC4 in both software and hardware are extremely easy to develop.
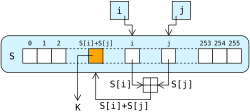
The RC4 encryption algorithm is started with a different key length, usually between 40 and 256 bits, using the key-scheduling algorithm (KSA). Once this has been completed, the stream of encrypted bits is created using the pseudo-random generation algorithm (PRGA).
RC4 fails the standards set by cryptographers for a secure cipher in many ways, and is not recommended for use in new applications as there are a lot of methods of attacking RC4. Dropping the first kilobyte of data from the keystream can improve the security somewhat.
RC4-based cryptosystems
- WEP
- WPA
- BitTorrent protocol encryption
- Microsoft Point-to-Point Encryption
- Secure Sockets Layer (optionally)
- Secure Shell (optionally)
- Remote Desktop Client (RDC over RDP)
- Kerberos (optionally)
- SASL Mechanism Digest-MD5 (optionally)
- Gpcode.AK, an early June 2008 computer virus for Microsoft Windows, which takes documents hostage for ransom by obscuring them with RC4 and RSA-1024 encryption
Where a cryptosystem is marked with "(optionally)", RC4 is one of several ciphers the system can be set to use.
RC4 Media
Related pages
- Advanced Encryption Standard
- Data Encryption Standard (DES)
- DES-X
- eSTREAM - An evaluation of new stream ciphers being conducted by the EU.
- TEA, Block TEA also known as eXtended TEA and Corrected Block TEA - A family of block ciphers that, like RC4, are designed to be very simple to implement.
- Triple DES (TDES)
References
- ↑ Rivest FAQ
- ↑ Cypherpunks mailinglist (1994-09-09). "Thank you Bob Anderson". Archived from the original on 2001-07-22. Retrieved 2007-05-28.
Other websites
RC4
- IETF Draft - A Stream Cipher Encryption Algorithm "Arcfour"
- Original posting of RC4 algorithm to Cypherpunks mailing list Archived 2008-02-07 at the Wayback Machine
- SCAN's entry for RC4
- Attacks on RC4 Archived 2015-02-21 at the Wayback Machine
- RC4 - Cryptology Pointers by Helger Lipmaa Archived 2008-10-14 at the Wayback Machine
- RSA Security Response to Weaknesses in Key Scheduling Algorithm of RC4 Archived 2004-12-10 at the Wayback Machine
- T-SQL implementation
RC4 in WEP